PURPOSE
• Analyze captured traffic and report any suspicious activity or successful attack.
Background / Scenario
Network Security team observed some suspicious activities from a PC inside a network and captured traffic between that PC and other computers in the same network.
IP address of the PC is known and captured files have been shared with you to analyze traffic to identify suspicious activities, any successful attack and access to company’s data.
IP address of the suspicious PC is 192.168.2.111
I. Is there any suspicious activity? Explain your findings.
We need to set up our environment first.
First will add “tcp.stream”, “http.host”
and “Geo IP” to the Wireshark.
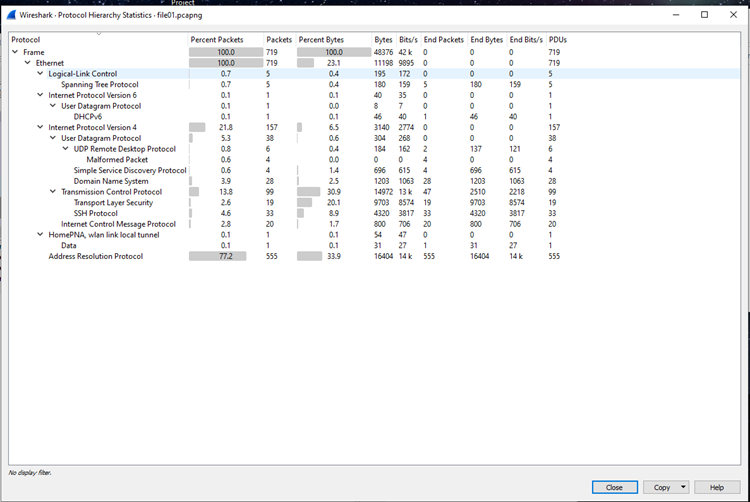
Then we can start by looking at the Protocol Hierarchy of each PCAP to gain a sense of what protocols are each being used the most.
File 01:
File 02:
File 04:
File 05:
File 06:
File 07:
According to my findings, each file pcap seems to have a different scenario.
There are several lines on file01, file 02, file04 and file05 where a network packet capture shows an SSH encrypted packet being sent from IP address 192.168.2.111 to IP address 192.168.2.77.
The packet capture indicates that the packet is encrypted and has a length of 128 bytes. The "Server:" field in the packet capture indicates that this packet is being sent from the server side of the SSH connection.
This might be the attacker trying to send malware via SSH
II. IP address of the targeted computer(s).
Using the filter expression ip.src==192.168.2.111 and tcp.flags.push == 1 will show you all the packets in the capture where the source IP address is 192.168.2.111 and where the PSH flag is set in the TCP header. This is useful for analyzing traffic originating from a particular device on the network and identifying potential issues with real-time data transfer.
file01
file07
After running the filter on all the PCAPs, we can see that the IP addresses of the targeted computers are:
192.168.2.77
192.168.2.108
III. Is there any attempt to access the resources inside the network? If yes, was it successful or no.
On file06.pcapng there is evidence of numerous request attempts at logging in. This is a sign of a brute force attack.
In file06 there was an http packet that had suspicious information.
<script src="/steal/steal.production.js?steal-built/production.js"></script>
This is a script tag that includes a JavaScript file named "steal.production.js" located in the root directory of the web server. The file path after the script tag indicates that the JavaScript file is being loaded from the same server as the web page.
The JavaScript file itself is named "steal-built/production.js", which suggests that it is a production-ready version of a JavaScript framework or library called "Steal". This framework is commonly used for managing dependencies and building JavaScript applications.
For file07.pcapng Yes, there was an FTP with the command USER where the argument was student. It seems the target was a payment.txt file.
IV. Name of the file(s) or resources that attacker was able to access in the attack, if there was any.
On this line:
417 1410.590502 192.168.2.108 192.168.2.111 FTP 78 Response: 226 Transfer complete. 1
The transfer request succeeded. The attacker obtained the payment.txt file.