Executive Summary
Following an incident involving the theft of a proprietary digital asset, the "Szechuan Sauce", a digital forensics investigation was initiated. Our preliminary assessment confirmed a security breach targeting their domain controller. Two primary systems—a server and a desktop—appeared compromised. Early indicators suggest possible malware involvement, with potential access or theft of other critical data beyond the Szechuan Sauce. This report will cover the assessment of the breach and the methodologies we used to perform a comprehensive analysis of the digital forensic evidence following the incident.
Objectives
1. Determine the operating systems of the server and desktop.
2. Ascertain if a breach occurred and its nature.
3. Understand the attack vector and any malware used.
4. Investigate any associated malicious IP addresses.
5. Identify the attacker's movements and accessed systems.
6. Explore the network layout and suggest immediate architecture changes.
7. Find out if the Szechuan sauce or other sensitive files were accessed or stolen.
Investigation Overview
Client Interview
The incident's victim is Rick Sanchez. Key points from the interview:
· Affected files were on the File Server on the Domain Controller.
· Rick is unaware of the exact OS version of the server.
· Systems were located in a 10.42.x.x network.
· Rick is concerned about specific files, including a secret about Beth.
Artifacts
The following sources are provided for the investigation:
· Disk Images (E01): DC01 and Desktop.
· Memory and PageFile: DC01 and Desktop.
· Autoruns: DC01 and Desktop.
· Protected Files: DC01 and Desktop.
· Network Traffic: Case001 PCAP.
Timeline
Setup and Preliminary Data Analysis
Run Volatility through the CMD Line
Run the Volatility command on the citadel memdump
volatility_2.6_win64_standalone>volatility_2.6_win64_standalone.exe imageinfo -f citadeldc01.mem
volatility_2.6_win64_standalone.exe --profile=Win2012R2x64 pslist -f citadeldc01.mem
We can look for foreign Ips in the netstat output
We have stumbled upon an IP that is unfamiliar
203.78.103.109:443
We will now run the malfind function of volatility
It looks like there is an executable being injected into the spoolsv.exe process
Next we will use the floss tool on the processes. Below is the output on the floss execution
Technical Findings
Answers:
1. What’s the Operating System of the Server?
Answer: Windows Server 2012
Methodology:
For this we are using the tool Autopsy. Since we have the image file, we will open the image file in Autopsy. Once we open the file, we will find all the information about the image, and as you can see from the screen shot below, we also found the OS the server is running on.
2. What’s the Operating System of the Desktop? Answer: Windows 10
Methodology:
We will follow the same steps but instead of using the DC01 image we will be using DESKTOP-E01. And as you can see from the screenshot below, we found the OS.
3. What was the local time of the Server?
Answer: Pacific Standard TimeMethodology:
For this we will be using Registry Explorer. As we know timestamps are usually stored in the REGISTRY, we can use Registry Explorer to go through the file. Since we are already provided with the files, in this case it’s the DC01-Protected file. We then drag and drop the files into the Registry Explorer application.
As you can see from the screenshot below, we found the local time zone.
4. Was there a breach?
Answer: Yes
Methodology: All points of analysis indicate that there was indeed a breach. The next questions and answers will elaborate on this.
5. What was the initial entry vector (how did they get in)?
Answer: Initial process was carried out by Brute Force.
Methodology:
The reason why it is brute force is simply due to multiple SYN requests to the same destination port.
6. Was malware used? If so, what was it? If there was malware answer the following:
a. What process was malicious?
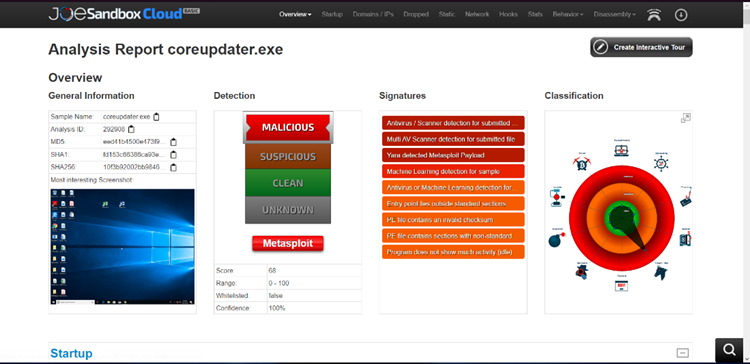
Answer: coreupdate.exe
Methodology:
Once we found out the malicious IP was 192.61.24.102, we used Wireshark to find out more about this process. After applying the necessary filters, we found out that there was a GET request from the malicious IP for an application.
After we exported the HTTP request and tried to run it on our system to get the hash value, our antivirus (in this case Windows Defender) flagged it as virus.
b. Identify the IP Address that delivered the payload.
Answer: 194.61.24.102
c. What IP Address is the malware calling to?
Answer: 203.78.103.109:443.
Since we already know the process name, we can use netscan in volatility and get the IP address.
d. Where is this malware on disk?
Answer: C:\Windows\System32\coreupdater.exe
e. When did it first appear?
Answer: 2020-09-19 03:56:37 UTC+0000
f. Did someone move it?
Answer: We know is it was moved to C:\Windows\System32\coreupdater.exe
g. What were the capabilities of this malware?
Answer: Metasploit it is versatile. In this case, Metasploit is dangerous because it provides a powerful and user-friendly platform for exploiting vulnerabilities in computer systems. In the hands of malicious actors, it can be used to gain unauthorized access, deliver harmful payloads, or spread malware.
h. Is this malware easily obtained?
Answer: Yes, as it is Metasploit it is free to download.
i. Was this malware installed with persistence on any machine?
When?Answer:2020-09-19 03:27:49
Where?
Answer: The coreupdater.exe is a runtime process which will start automatically when the computer is on.
7. What malicious IP Addresses were involved?
Answer: Evidence Suggests 194.61.24.102 & 203.78.103.109.
a. Were any IP Addresses from known adversary infrastructure?
Answer: These IP are from the Netherlands and Thailand. Foreign agents or actors trying to gain information. It was also flagged in VirusTotal.
b. Are these pieces of adversary infrastructure involved in other attacks around the time of the attack?
Answer: Yes, they were flagged for other malicious activities discovered through online IP analysis tools.
8. Did the attacker access any other systems?
a. How?
Answer: Analysis of the PCAP through wireshark reveals the RDP connections from domain controller and the desktop. The attacker gained RDP access to C137\DESKTOP-SDN1RPT$
b. When
Answer: The PCAP analysis showed it was on 2020-09-19 at 03:36:24
c. Did the attacker steal or access any data?
According to analysis the files in the secret folder were all recently accessed.
When?
Answer: 2020-09-19
9. What was the network layout of the victim network?
Answer: The network 10.42.85.0/24 has a layout that mainly consists of a Domain Controller and an endpoint
10. What architecture changes should be made immediately?
Considering the initial breach resulted from a brute-force RDP attack on the DC, immediate action should be taken to disable RDP access to the DC from external sources. RDP access to the DC should be restricted exclusively to users within the local network.
11. Did the attacker steal the Szechuan sauce? If so, what time?
Answer: The attacker was able to obtain the recipe for the Szechaun sauce at 3:32:21 am
12. Did the attacker steal or access any other sensitive files? If so, what times?
Answer: Along with the secret sauce, the attacker also deleted the SECRET_beth.txt file as witnessed in the recycle bin.
13. Finally, when was the last known contact with the adversary?
Answer: The most latest logoff time was at 2020-09-09 at 12:52:11 AM
Advanced and Bonus Questions
1. What CIS Top 20 or SANS Top 20 Controls would have directly prevented this breach?
Source: https://www.cisecurity.org/controls/cis-controls-list
https://www.cm-alliance.com/consultancy/compliance-gap-analysis/sans-top-20-controls/
CIS Control 1: Inventory and Control of Enterprise Assets
Ensuring all assets are inventoried and controlled can prevent unauthorized devices from accessing the network or being utilized in malicious activities.
CIS Control 4: Secure Configuration of Enterprise Assets and Software
Proper configuration can prevent exploitable vulnerabilities. This might have stopped the RDP brute force if RDP was securely configured or disabled.
CIS Control 5: Account Management
Proper account management, including strong passwords, would prevent or slow down brute force attacks.
CIS Control 6: Access Control Management
Ensuring that only the necessary individuals have access to systems and data can prevent breaches. This would have limited the scope of the attack once the attacker had gained initial access.
CIS Control 7: Continuous Vulnerability Management
Regular scanning and patching of vulnerabilities would reduce the risk of exploit. This might have detected open and vulnerable services like RDP.
CIS Control 8: Audit Log Management
Proper logging can provide early detection of malicious activities. If logs were actively monitored, the brute force attack or unauthorized access might have been detected in real-time.
CIS Control 9: Email and Web Browser Protections
Implementing strict browser configurations could have prevented the downloading of malicious tools like Meterpreter.
CIS Control 10: Malware Defenses
Tools that detect and block malware would have helped in preventing the Meterpreter download or its execution.
CIS Control 13: Network Monitoring and Defense
Active network monitoring can detect abnormal patterns, such as exfiltration of data or lateral movements.
CIS Control 16: Application Software Security
Ensuring that software, especially those exposed to the internet like web servers, is secure is crucial. This might have mitigated the use of tools like Hydra and Meterpreter.
2. What major architecture improvement could be made that would have prevented this breach?
Answer: Significant architectural improvements that could be implemented to prevent potential breaches include implementing a Virtual Private Network (VPN) to ensure encrypted and secure remote access to the network, deploying an Intrusion Prevention System (IPS) to monitor and block malicious traffic in real-time, and utilising an external firewall to create a robust barrier against unauthorised external access while filtering out potentially harmful traffic. These techniques, when combined, form a multi-layered defence strategy, reinforcing the network against a wide spectrum of cyber threats.
3. Can you identify policy improvements or controls that should be implemented to secure this environment?
Answer: Policies should require increasing password complexity by adding requirements like needing a minimum of 10 characters, small letter, capital letter, special character and a number. Also ban password reuse to improve environmental security. Furthermore, deploying an external firewall and an Intrusion Prevention System (IPS) will strengthen perimeter defence, while an Endpoint Detection and Response (EDR) solution ensures real-time monitoring and response to threats at the device level, resulting in a comprehensive and layered security strategy.
4. Which users have actually logged onto the DC?
Answer: Administrator
Usually to know which users have logged onto a system, we would look into the C:\Users directory and based on that, we can see that user Administrator was logged into the system.
5. Which users have actually logged onto the Desktop machine?
Answer: Admin, Administrator and Rick Sanchez
Like the previous step, to check who was logged on to the desktop, we look into the C:\Users Directory.
6. What are the passwords for the users in the domain?
Passwords are stored in a hash in the SAM File
Usually on Windows, user passwords are stored on the same file which is located in C:\Windows\System32\config
7. Can you recover the original file about Beth’s Secrets?
a. What was the original name?
Answer: SECRET_beth.txt
After digging through the files in Autopsy, I managed to find a file related to beth in the recent documents folder, that file was pointing to C:\FileShare\Secret. When I accessed that location, the original file was there and was showing as deleted.
b. Original Contents?
Answer: Earth beth is the real beth.
The cross on the icon on Autopsy means the file might have been deleted, and when a file is deleted it usually goes to is Recycle Bin. Using FTK Imager, I opened the Recycle Bin directory and checked the file and one of them was of Beth, I clicked on it and it showed the original text.
8. Finally, what file was time stomped?
Answer: Beth_Secret.txt
Based on information on both Autopsy and FTK Imager, we can see that the file Beth_Secret.txt was time stomped because on FTK Imager the modified time is 11:35:35pm and autopsy, the metadata shows that the file was modified at 19:35:35. That could be an evidence of time stomping
Reference
https://www.oit.va.gov/Services/TRM/files/RegistryExplorerManual.pdf
https://downloads.volatilityfoundation.org/releases/2.4/CheatSheet_v2.4.pdf
https://www.cm-alliance.com/consultancy/compliance-gap-analysis/sans-top-20-controls/